python解析windows日志文件,查询服务器是否被人攻击
最近大致浏览了下windows server的日志记录,发现有不少的异地IP进行了登录尝试,而且有部分是登录成功的,但不确定是否本人自己登陆,所以借助python,对日志进行解析,并根据IP查询其远程物理地址。
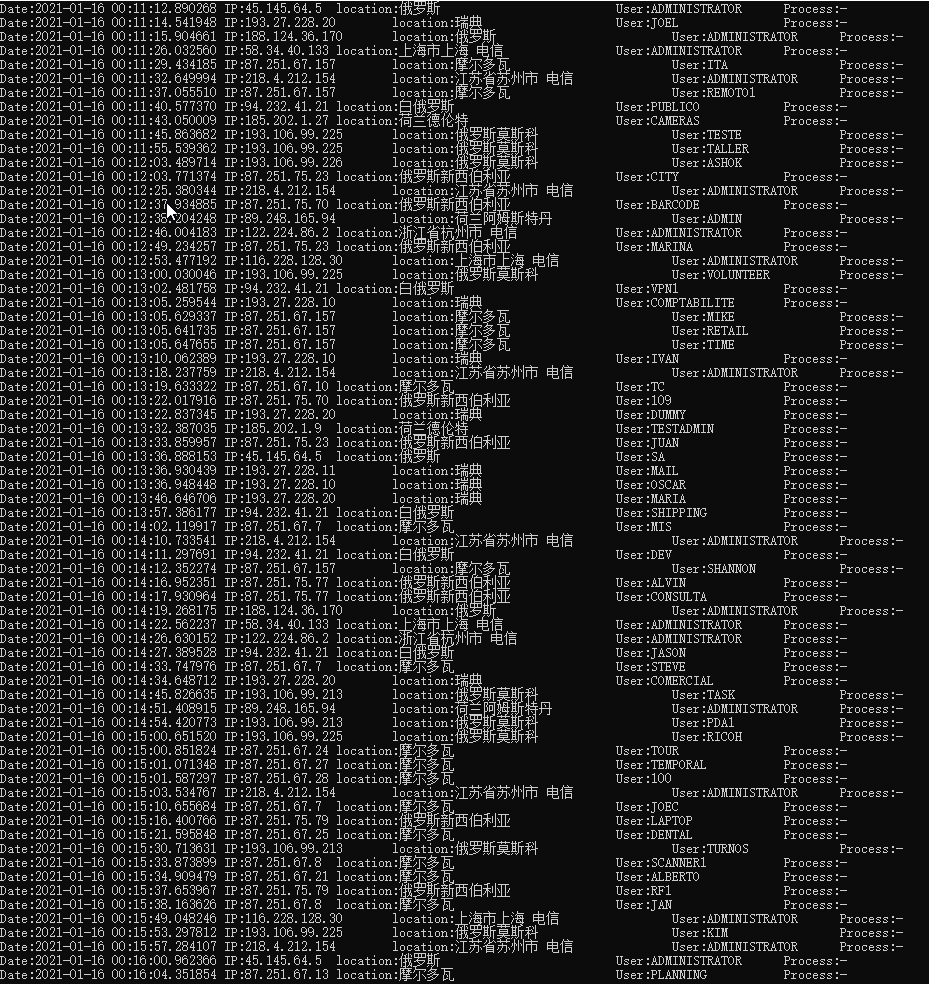
最终效果:
【MD,老毛子就是天天在扫描,爆破密码,即使改了端口还是在枚举】
大致代码如下:
D:\share\1.evtx 为日志导出文件
原创文章,转载请注明出处:
http://30daydo.com/article/44130
完整代码,可以通过公众号回复: windows日志解析获取

最终效果:
【MD,老毛子就是天天在扫描,爆破密码,即使改了端口还是在枚举】
大致代码如下:
import mmap
import contextlib
from Evtx.Evtx import FileHeader
from Evtx.Views import evtx_file_xml_view
from xml.dom import minidom
from ip_convertor import IP
import re
class WindowsLogger():
def __init__(self,path):
self.path = path
self.formator = 'IP:{:10}\tlocation:{:20}\tUser:{:15}\tProcess:{}'
def read_file(self):
with open(self.path,'r') as f:
with contextlib.closing(mmap.mmap(f.fileno(),0,access=mmap.ACCESS_READ)) as buf:
fh = FileHeader(buf,0)
return fh
return None
def parse_log_detail(self,filteID):
with open(self.path,'r') as f:
with contextlib.closing(mmap.mmap(f.fileno(),0,access=mmap.ACCESS_READ)) as buf:
fh = FileHeader(buf,0)
for xml, record in evtx_file_xml_view(fh):
#只输出事件ID为4624的内容
# InterestEvent(xml,4624)
for IpAddress,ip,targetUsername,ProcessName in self.filter_event(xml,filteID):
print(self.formator.format(IpAddress,ip,targetUsername,ProcessName))
# 过滤掉不需要的事件,输出感兴趣的事件
def filter_event(self,xml,EventID,use_filter=True):
xmldoc = minidom.parseString(xml)
# 获取EventID节点的事件ID
collections = xmldoc.documentElement
events=xmldoc.getElementsByTagName('Event')
for evt in events:
eventId = evt.getElementsByTagName('EventID')[0].childNodes[0].data
time_create = evt.getElementsByTagName('TimeCreated')[0].getAttribute('SystemTime')
eventData = evt.getElementsByTagName('EventData')[0]
for data in eventData.getElementsByTagName('Data'):
if data.getAttribute('Name')=='IpAddress':
IpAddress=data.childNodes[0].data
if data.getAttribute('Name')=='TargetUserName':
targetUsername = data.childNodes[0].data
if data.getAttribute('Name')=='ProcessName':
ProcessName = data.childNodes[0].data
if use_filter is True and eventId==EventID:
ip=''
if re.search('^\d+',IpAddress):
ip = IP(IpAddress).ip_address
yield IpAddress,ip,targetUsername,ProcessName
def main():
path=r'D:\share\1.evtx'
filter_id = '4624'
app = WindowsLogger(path)
app.parse_log_detail(filter_id)
if __name__ == '__main__':
main()
D:\share\1.evtx 为日志导出文件
原创文章,转载请注明出处:
http://30daydo.com/article/44130
完整代码,可以通过公众号回复: windows日志解析获取